What is Mobile Device Management (MDM)?
Mobile Device Management (MDM) stands as a crucial pillar for organizations aiming to maintain control, security, and efficiency over their mobile devices. As smartphones, tablets, and other mobile gadgets proliferate in both personal and professional spheres, the need to manage these devices effectively becomes ever more essential. Delve deep into the realm of Mobile Device Management, exploring its significance, functionalities, best practices, and its pivotal role in ensuring a seamless mobile experience for businesses worldwide.
Understanding Mobile Device Management
MDM is a comprehensive solution designed to streamline the management and security of mobile devices used for dedicated purposes. Encompasses a suite of tools and technologies aimed at managing various aspects of mobile devices, including configuration, security, monitoring, and maintenance. MDM empowers organizations to exert control over their mobile fleet, irrespective of whether the devices are company-owned or part of a Bring Your Own Device (BYOD) initiative.
Device Enrollment & Provisioning
Device enrollment is the initial step in MDM, where devices are registered and onboarded onto the management platform. Provisioning involves configuring devices with the necessary settings, applications, and security policies to align them with organizational standards.
Policy Management
MDM enables administrators to define and enforce policies governing device usage, security configurations, and access permissions. Policies can include requirements such as passcode complexity, encryption, app whitelisting/blacklisting, and compliance checks.
Application Management
MDM facilitates the distribution, installation, and management of applications across mobile devices. Administrators can remotely deploy, update, or remove applications to ensure compliance and productivity.
Security
Security features provided by MDM include data encryption, remote lock and wipe capabilities, and real-time threat detection. MDM safeguards sensitive corporate data from unauthorized access or breaches, mitigating potential risks associated with mobile usage.
Monitoring & Reporting
MDM platforms offer robust monitoring capabilities, allowing administrators to track device performance, usage patterns, and security incidents. Comprehensive reporting tools provide insights into device compliance, policy violations, and potential areas for optimization.
Enforce Restrictions
MDM empowers administrators to disable factory resetting the device, enabling/disabling Bluetooth/WiFi, restrict sharing mobile data and USB access. Choose screen brightness, disable notification bar and hardware buttons (volume/power buttons).
What is MDM?
How About Exploring Our Mobile Device Management Features?
Let our product experts get back to you and have all your queries cleared. You'd get more clear understanding on what you are looking for once we understand your requirements!
Benefits of Mobile Device Management
Enhanced Security
MDM strengthens the security posture of organizations by enforcing stringent security policies and safeguards. It protects sensitive data from unauthorized access, malware threats, and other cybersecurity risks, thereby mitigating potential breaches.
Improved Compliance
Compliance with regulatory standards and industry-specific mandates is paramount for organizations operating in regulated sectors. MDM assists in ensuring compliance by enforcing security protocols, tracking device usage, and generating compliance reports as needed.
Cost Efficiency
Effective management of mobile devices results in cost savings through optimized resource utilization and reduced downtime. MDM minimizes the risk of data loss or security breaches, mitigating potential financial losses associated with such incidents.
Increased Productivity
By automating device management tasks and ensuring seamless access to resources, MDM enhances workforce productivity. Employees can focus on their core tasks without being hindered by device-related issues or security concerns, leading to greater efficiency.
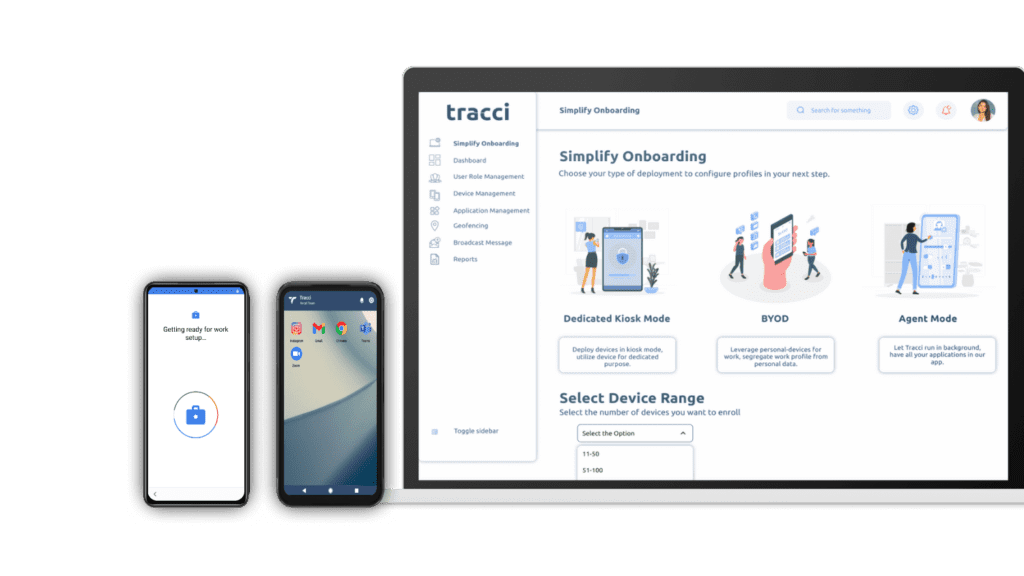
MDM Deployment
Best Practices for Mobile Device Management
Adhere to best practices, and maximize the effectiveness of Mobile Device Management initiatives.
Improve Productivity
Eliminate Downtime
Define comprehensive policies governing device usage, security configurations, and acceptable behaviors. Communicate these policies to all stakeholders and ensure ongoing compliance through regular audits and enforcement mechanisms.
Perform periodic risk assessments to identify potential vulnerabilities and security gaps within the mobile environment. Address identified risks promptly through proactive measures such as software updates, patches, and policy adjustments.
Educate employees on the importance of mobile security, best practices for device usage, and common security threats. Offer training sessions, awareness campaigns, and resources to empower users to make informed decisions regarding mobile security.
Adopt a multi-layered approach to security, incorporating measures such as device encryption, network security, and application-level protections. Leverage advanced security technologies such as Mobile Threat Defense (MTD) solutions to detect and mitigate emerging threats proactively.
Role of MDM
Future Trends in Mobile Device Management
Zero Trust Security
The Zero Trust model, which assumes no implicit trust for any user or device, is gaining traction as organizations seek to bolster their security postures. MDM solutions will increasingly incorporate Zero Trust principles, emphasizing continuous verification and least privilege access controls.
Integration with Endpoint Security
Integration between MDM and endpoint security solutions will become more seamless, enabling organizations to adopt a holistic approach to device and data protection. Unified platforms offering comprehensive endpoint management capabilities will emerge to address evolving security challenges.
AI and Automation
Artificial Intelligence (AI) and automation technologies will play a significant role in enhancing the efficiency and efficacy of MDM operations. Predictive analytics, anomaly detection, and automated remediation will streamline device management tasks and proactively address security threats.