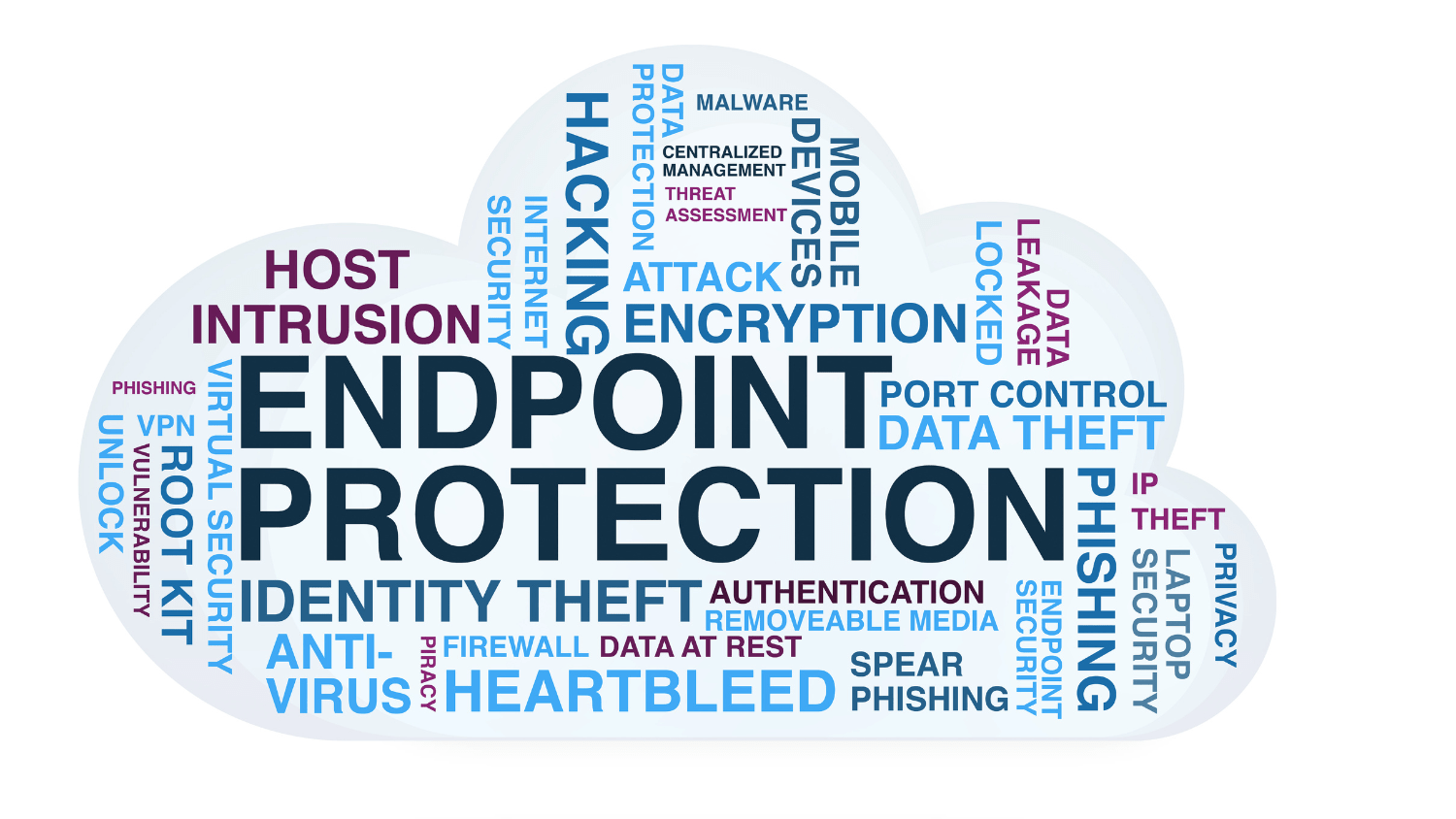
What is Endpoint Security? Role of MDM in Endpoint Security
The rapidly evolving landscape of cybersecurity challenges organizations to stay away from a multitude of threats targeting their digital assets. Endpoint security is a crucial aspect of cybersecurity, which focuses on securing individual devices connected to a network. This essay explores the concept of endpoint security, its significance in modern cybersecurity, and the role of Mobile Device Management (MDM) solutions as a critical component in addressing endpoint security challenges.
What is Endpoint Security: An Overview
Endpoint security refers to the protection of endpoints or individual devices such as desktops, laptops, smartphones, tablets, servers, and other Internet of Things (IoT) devices from cyber threats. Endpoints serve as entry points for attackers seeking unauthorized access to a network, making them vulnerable targets for various forms of malware, ransomware, phishing attacks, and data breaches.
The importance of endpoint security has surged with the proliferation of remote work and Bring Your Own Device (BYOD) policies in organizations. Employees accessing corporate networks from diverse locations and using personal devices pose significant challenges for IT security teams. Consequently, securing these endpoints has become paramount to safeguarding sensitive data and ensuring business continuity.
Also read: Difference between BYOD, COPE, COBO, CYOD
Components of Endpoint Security
Effective endpoint security encompasses a range of technologies and strategies designed to detect, prevent, and respond to cyber threats targeting endpoints. Some key components of endpoint security include:
- Antivirus and Anti-malware Software: These programs scan devices for known malware signatures and behavior patterns, quarantining or removing malicious files to prevent infections.
- Firewall Protection: Firewalls monitor incoming and outgoing network traffic, filtering potentially harmful data packets and blocking unauthorized access attempts.
- Intrusion Detection and Prevention Systems (IDPS): IDPS solutions detect and thwart suspicious activities and intrusion attempts on endpoints by analyzing network traffic and system logs.
- Data Encryption: Encrypting sensitive data stored on endpoints and during transmission helps prevent unauthorized access and data breaches.
- Patch Management: Regularly updating software applications and operating systems with security patches is crucial to address known vulnerabilities and reduce the risk of exploitation by attackers.
- Endpoint Detection and Response (EDR): EDR solutions provide real-time monitoring, threat detection, and incident response capabilities to identify and mitigate advanced threats targeting endpoints.
Challenges in Endpoint Security
Despite advancements in endpoint security technologies, organizations encounter several challenges in effectively securing their endpoints:
- Endpoint Diversity: The proliferation of devices with diverse operating systems, form factors, and usage patterns complicates endpoint management and increases the attack surface for cyber threats.
- Bring Your Own Device (BYOD): BYOD policies introduce additional complexities as organizations struggle to balance employee productivity and convenience with security requirements.
- Remote Workforce: The shift towards remote work in response to global events has amplified endpoint security concerns, as remote employees access corporate networks from unsecured environments.
- Advanced Threats: Cybercriminals continually evolve their tactics, leveraging sophisticated malware variants and zero-day exploits to evade traditional endpoint security defenses.
- Insider Threats: Malicious insiders or negligent employees pose a significant risk to endpoint security, potentially compromising sensitive data or sabotaging systems from within.
Mobile Device Management (MDM) Solutions: Addressing Endpoint Security Challenges
Mobile Device Management (MDM) solutions emerge as a comprehensive approach to addressing the challenges associated with endpoint security, particularly in environments characterized by device diversity, remote work, and BYOD policies. MDM solutions enable organizations to centrally manage and secure mobile devices, enforce security policies, and streamline device provisioning and configuration. Below are some key features and benefits of MDM solutions in enhancing endpoint security:
- Device Inventory and Tracking: MDM solutions maintain an inventory of managed devices, providing visibility into device attributes, configurations, and usage statistics. Additionally, MDM platforms enable organizations to track the physical location of devices, aiding in asset management and loss prevention.
- Kiosk Lockdown/Policy Enforcement: MDM solutions allow administrators to lock devices in kiosk mode, define and enforce security policies across managed devices, ensuring compliance with organizational standards and regulatory requirements. These policies may include password complexity rules, device encryption settings, application whitelisting, and remote wipe capabilities in case of loss or theft.
- Secure Mobile Access: MDM platforms facilitate secure access to corporate resources and data from mobile devices, utilizing technologies such as Virtual Private Networks (VPNs), multi-factor authentication (MFA), and containerization to protect sensitive information from unauthorized access or interception.
- Application Management: MDM solutions enable organizations to manage the lifecycle of mobile applications, including distribution, installation, updates, and removal. By implementing app whitelisting and blacklisting policies, organizations can control the types of applications permitted on managed devices, reducing the risk of malware infections and data leakage.
- Mobile Threat Defense: Some advanced MDM solutions incorporate Mobile Threat Defense (MTD) capabilities, leveraging machine learning algorithms and threat intelligence feeds to detect and mitigate mobile-specific threats such as malicious apps, network attacks, and phishing attempts.
- Remote Management and Troubleshooting: MDM platforms offer remote management capabilities, allowing administrators to perform tasks such as device provisioning, configuration changes, software updates, and troubleshooting without physical access to the device. This feature is particularly valuable in supporting remote employees and minimizing downtime.
- Compliance and Reporting: MDM solutions assist organizations in maintaining regulatory compliance by generating audit trails, compliance reports, and device usage analytics. These insights help demonstrate adherence to security standards and facilitate risk management processes.
Endpoint security remains a critical priority for organizations seeking to safeguard their digital assets and mitigate cyber risks. In an era characterized by increasing device diversity, remote work, and evolving threat landscapes, Mobile Device Management (MDM) solutions emerge as a vital component in addressing endpoint security challenges. By providing centralized management, policy enforcement, threat detection, and compliance capabilities, MDM solutions empower organizations to enhance the security posture of their endpoints and adapt to the dynamic nature of modern cybersecurity threats. As organizations continue to embrace digital transformation initiatives, investing in robust endpoint security measures, including MDM solutions, becomes imperative to protect against cyber threats and preserve business resilience.
Comments are closed